Cybersecurity Landscape on Remote State Estimation: A Comprehensive Review
Jing Zhou,,, Jun Shang,,, and Tongwen Chen,,
Abstract—Cyber-physical systems (CPSs) have emerged as an essential area of research in the last decade, providing a new paradigm for the integration of computational and physical units in modern control systems.Remote state estimation (RSE) is an indispensable functional module of CPSs.Recently, it has been demonstrated that malicious agents can manipulate data packets transmitted through unreliable channels of RSE, leading to severe estimation performance degradation.This paper aims to present an overview of recent advances in cyber-attacks and defensive countermeasures, with a specific focus on integrity attacks against RSE.Firstly, two representative frameworks for the synthesis of optimal deception attacks with various performance metrics and stealthiness constraints are discussed, which provide a deeper insight into the vulnerabilities of RSE.Secondly, a detailed review of typical attack detection and resilient estimation algorithms is included, illustrating the latest defensive measures safeguarding RSE from adversaries.Thirdly, some prevalent attacks impairing the confidentiality and data availability of RSE are examined from both attackers’ and defenders’ perspectives.Finally, several challenges and open problems are presented to inspire further exploration and future research in this field.
I.INTRODUCTION
THE last decade has witnessed rapid progress in the development of cyber-physical systems (CPSs), which are tight integrations of computational, networking, and physical components.CPSs provide a general modeling framework that covers various industrial processes and critical infrastructures,e.g., power grids [1], water distribution networks [2], intelligent transportation systems [3], smart medical devices [4], and industrial control systems [5].The safe and efficient operation of CPSs depends significantly on the reliable transmission of data packets, which could be manipulated craftily by malicious agents particularly if wireless networks are deployed.Stuxnetis one such well-known cyber-worm that caused great damage to nuclear facilities in Iran by injecting falsified control commands [5].In 2015, a synchronized and coordinated cyber-attack compromised three Ukrainian regional electric distribution companies, resulting in power outages affecting approximately 225 000 customers for several hours [6].A recent cyber-attack that crippled the largest fuel pipeline in the U.S.and led to energy shortages across the east coast was another prominent example [7].These realworld incidents evidently indicate the necessity and urgency to explore the inherent vulnerabilities of CPSs and develop defensive countermeasures against cyber-attacks.
The security of CPSs can be conceptualized as comprising three primary facets in Fig.1: integrity, availability, and confidentiality.Correspondingly, the cyber-threats that undermine these attributes are respectively termed as false-data injection(FDI), denial-of-service (DoS), and eavesdropping attacks[8]–[10].Among these, FDI and DoS attacks have constituted the predominant share of real-world incidents and have been the central focus of academic research in CPS security for the past decade.In DoS attacks, adversaries disseminate noisy packets to obstruct communication channels among data terminals, thereby rendering valuable information inaccessible to the intended recipients [11], [12].FDI attacks, also referred to as integrity attacks, demand more substantial resources for practical implementation.Adversaries must infiltrate communication links to alter original packets or insert falsified data.In both scenarios, CPS nominal performance undergoes significant deterioration, potentially resulting in increased control costs [13], diminished state estimation quality [14], and even instability within closed-loop systems [15].Eavesdropping attacks, while seemingly less intrusive since the attacker’s actions do not directly impact system performance, can still have devastating consequences owing to the leakage of critical information [16], [17].Other less frequently encountered cyber threats in the industrial realm encompass topology poisoning, load redistribution, and data framing attacks [18].Despite the inevitability of these malicious disruptions, adversaries are typically unable to execute uncontrolled attacks due to the countermeasures employed by system defenders, such as virus firewalls, anomaly detectors, and data encryption mechanisms [19]–[21].Moreover, the limited resource budgets of adversaries and their restricted access to secure information also narrow down the spectrum of feasible attack policies.

Fig.1.Three facets of CPS security.
Remote state estimation (RSE) is an essential functional module in CPSs.The primary objective of RSE is to derive estimates of physical processes based on measurements collected remotely, such as from sensors or cameras, without necessitating direct physical access.In practical applications,state estimates are usually utilized for feedback control and operation status monitoring, underscoring the pivotal role of RSE in ensuring the safe and efficient operation of industrial facilities.Nevertheless, the discerption of estimators and physical units renders it easier for adversaries to launch cyberattacks compared to integrated systems.Recently, it has been demonstrated in numerous publications that adversaries can manipulate data packets transmitted through unreliable channels of RSE, resulting in significant degradation of estimation performance and the leakage of confidential information [22],[23].While the field of fault detection and fault-tolerant control has witnessed the application of effective algorithms for anomaly detection and enhancing the resilience of physical systems [24], these methods may fail to defend against cyberattacks.Transmission or component failures are usually considered as physical events that affect the performance of RSE in an uncoordinated manner, rendering them relatively easy to detect.On the contrary, cyber-attacks are ingeniously designed by intelligent adversaries, making their detection and mitigation a much more challenging task.
In the field of smart grids, Liuet al.discovered that by introducing falsified data into the sensor channels, it was possible to greatly amplify the error of least square estimators [1].Moreover, this attack had the capability to completely evade detection by residual-based bad-data detectors.While their primary focus was on least-square estimators, this investigation can be considered as the pioneering effort that ignited widespread research on the vulnerabilities of RSE.The relevant investigation has been extended from static systems in smart grids to dynamic ones in networked control systems.The estimators that are examined consist of both least square estimators and Luenberger observers.In situations where the process and measurement noises follow Gaussian distributions, Kalman filters are typically employed to attain optimal state estimates with minimal mean-square errors.Recently,numerous publications have delved into the examination of security concerns pertaining to a wide array of topics, including event-triggered estimators [25]–[27], distributed estimators [28]–[30], multiple-sensor systems [31], [32], RSE in nonlinear plants [33], [34], and other forms.
The existing research concerning vulnerabilities of RSE can be broadly classified into two main categories:
Problem 1: Design of worst-case attacks: This category focuses on developing attacks that are optimized subject to stealthiness and/or energy constraints.These studies seek to identify the most effective strategies for degrading system performance, primarily from the perspective of adversaries.
Problem 2: Attack detection/identification and resilient estimation algorithms: This category is dedicated to developing methods for detecting and identifying attacks, as well as creating resilient estimation algorithms.These efforts aim to mitigate the impacts of attacks, primarily from the standpoint of defenders.
Due to practical restrictions, the synthesis of optimal attacks and defensive countermeasures often takes the form of a constrained optimization problem.This problem seeks to maximize the benefit of an agent, whether an attacker or a defender, while adhering to stealthiness, resource budget, and information constraints [23], [35].There are also some studies assuming that the dynamic actions of both attackers and defenders are known to each other.Consequently, each side can react optimally based on their opponent’s actions.The decision-making process for both parties is explored within the framework of game theory [36]–[38].
To provide an up-to-date perspective on the current state of research and to stimulate further exploration in this area, this paper aims to provide an extensive overview of recent developments in the model-based synthesis of cyber-attacks against RSE and defensive countermeasures.In contrast to many existing surveys that cover a broader range of cyber-attacks,including aspects such as control performance loss, attackresilient control, or domain-oriented reviews [4], [7], [18],[19], [21], [39]–[46], this paper is dedicated to a more detailed examination on the performance degradation of RSE and the defense techniques.A comparison of recent surveys on cybersecurity of CPSs is listed in Table I.
The remainder of this paper is organized as follows.Section II describes the system model and formulates the problem of cyber-attacks against RSE.Section III discusses the synthesis of integrity attack strategies with various performance metrics and stealthiness/energy constraints.Section IV reviews the representative defensive measures against cyberattacks.Section V briefly discusses other types of attacks that affect data confidentiality and availability of RSE.Finally,Section VI concludes the discussion and addresses some challenging issues related to this topic.
II.SYSTEM MODEL AND PROBLEM SETUP
The system configuration of RSE is illustrated in Fig.2.The process dynamics are characterized by a discrete linear timeinvariant (LTI) system:
wherexkandykrepresent the state and sensor measurement,respectively;wkandvkare the process and measurement noises, respectively.In the majority of existing works,wkandvkare assumed to be zero-mean independent and identically distributed (i.i.d.) Gaussian noises with known covariances.Therefore, a standard Kalman filter without packet dropouts and delays can be employed at the remote end to estimate system states.Letxk|kdenote thea posterioriminimum meansquare error (MMSE) state estimate andPk|kthe corresponding estimation error covariance,
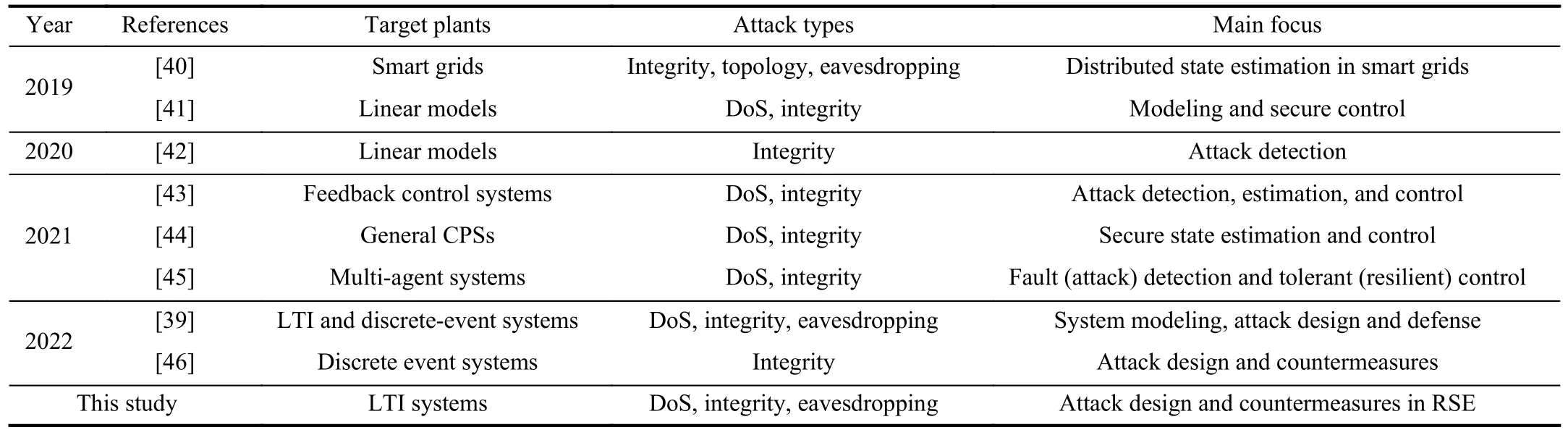
TABLE I RELATED SURVEYS ON CYBERSECURITY OF RSE
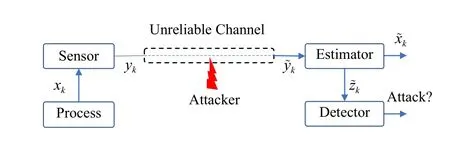
Fig.2.System configuration of RSE.
then the state estimation quality, also known as the performance of RSE, can be measured by Trace(Pk|k).To reveal potential faults or attacks within physical units and transmission channels, a residual-based anomaly detector is typically deployed in parallel with RSE and generates a binary alarm sequence according to
wherezk=yk-Cxk|k-1is called innovation or residual,xk|k-1represents thea prioristate estimates of RSE, and δ>0 is a defender-specified scalar that controls the false-alarm rate(FAR) at nominal conditions;gk(·) is the evaluation function that takes various forms depending on the statistical properties ofwkandvk.Ifgk(zk) exceeds a given detection threshold,an alarm indicating the occurrence of abnormal events will be raised (Ak=1).As will be discussed in the next section, the different selections of the functiong(k) result in two popular frameworks for the design of so-called stealthy integrity attacks.
In this paper, our discussion primarily centers on the discrete-time LTI system in (1), a model that has been adopted by massive existing studies.This model serves as a fundamental structure that can be readily extended to various scenarios including multiple-sensor systems, distributed estimators, and event-based estimation.The control inputs are omitted in (1)because they do not affect the estimation quality if attacks are launched on only the sensor channel.
A. Attack Model
The above system configuration is standard in model-based fault detection [24].Nevertheless in Fig.2, what differentiates cyber-attacks from transmission faults is that the sensor outputs (yk, orzkfor smart sensors) in unreliable links can be intentionally eavesdropped on and altered by adversaries.Our ultimate objective is to safeguard RSE from malicious attacks.However, the ancient proverb “If you know both the enemy and yourself,you will fight hundreds of battles without a loss”highlights the importance of examining worst-case attacks that maximize the adversary’s advantage.InProblem 1, one assumes the perspective of an attacker and explores optimal strategies capable of causing the most significant degradation in estimation quality within RSE, taking into account various stealthiness and performance metrics.These studies are essential for uncovering vulnerabilities of RSE and laying the groundwork for the development of countermeasures.To this end, the following assumptions are often made to characterize the capabilities of potential adversaries.
1) An attacker knows all system parameters, noise statistics,and other necessary knowledge (system configuration, the type of anomaly detectors, etc.).
2) An attacker can eavesdrop on and/or modify the original data packets transmitted in unreliable channels.They may also be able to manipulate noise or interference power in transmission links.
These characteristics enable adversaries to launch FDI,DoS, and eavesdropping attacks.While powerful attackers may be rare in real-world scenarios, the above assumptions align withShannon’s maxim, asserting that a system’s security should not depend on its obscurity [47].Though it might be difficult in practice to obtain system parameters, we frequently adopt the perspective that adversaries can obtain them through methods such as system identification and controller intrusion.Stuxnet cyber-worm serves as a concrete example in the industrial realm [5].Only by assuming that attackers possess comprehensive knowledge of target facilities, we can investigate the impact of the worst-case attacks.
B. Performance Assessment and Stealthiness Metrics

2)Error Norm Related Performance: The compromised measurement is designed to cause a large difference between the corrupted and nominal state estimates.Some integrity attacks may cause the RSE to become unstable, leading to unbounded estimation errors.
From an adversary’s perspective, enabling integrity attacks to bypass anomaly detectors is one of their primary imperatives.In existing studies, different definitions of stealthiness can be categorized as:

The design of integrity attacks maximizing covariance related performance metrics subject to stochastic stealthiness will be discussed in Section III-A.The design of integrity attacks with estimation error norm related performance and deterministic stealthiness will be discussed in Section III-B.
III.OPTIMAL ATTACK STRATEGIES
In the following, two representative frameworks for the design of stealthy integrity attacks are discussed.The relevant studies and defensive measures are classified in Fig.3.
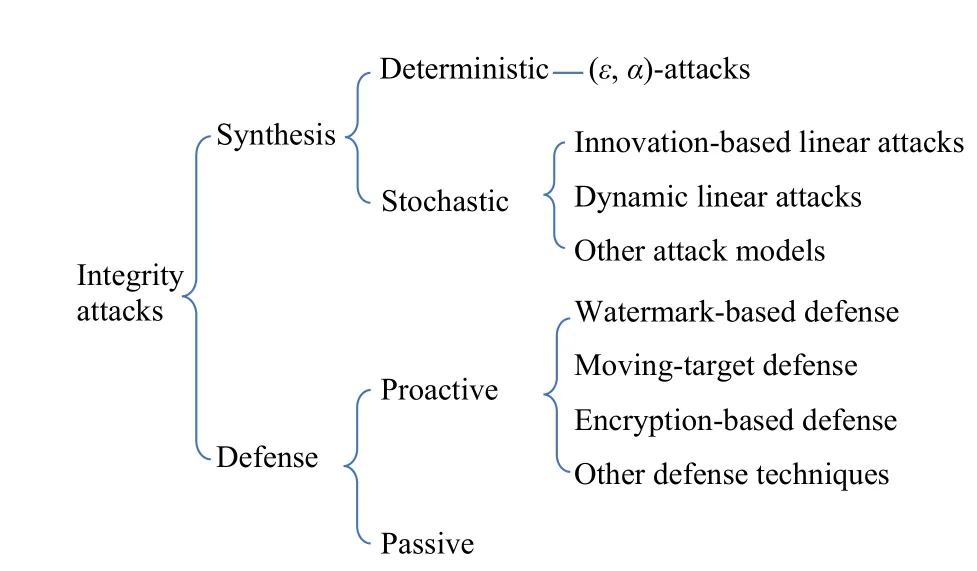
Fig.3.Synthesis and defensive measures for integrity attacks.
A. Stochastic Attacks
In this section, we examine different attacks aimed at maximizing the performance index associated with error covariance while adhering to stealthiness constraints based on statistical properties.Denote the set of eavesdropped data as
then creating an optimal attack involves determining a mapping from Ikto the space of sensor outputs, and obtaining its general form can be challenging.Note that synthesizing the compromised output) is equivalent to designingif the initial state of RSE is known to the adversary.Some earlier work frequently adopted linear attack models.Recently, general information-based attacks without the linearity assumption have also been derived.
1)Innovation-Based Static Linear Attacks: In the pioneering work [22], Guoet al.introduced an innovation-based linear attack that maximizesJg, where the compromised innovation is assumed to be a linear transformation of the currentstep nominal innovation, augmented by compensatory Gaussian white noises.It is then proved that the optimal attack strategy is simply inverting the sign of the nominal innovation.This interesting result has sparked extensive research endeavors since then; a majority of them lie in the following linear domain with different S [35], [48]–[53]:
where S is the index set of employed innovations;and Φkare parameters to be determined.The optimal attack in [22]led to an i.i.d.compromised innovation sequence, enabling it to deceive χ2detectors of arbitrary detection lengths.To strike a balance between attack performance and stealthiness, Li and Yang developed a linear attack that utilizes the current innovation and an additional historical one, positioned beyond the sliding window of χ2detectors [48].This modification enhanced the attack’s stealthiness, enabling it to deceive anomaly detectors that use a fixed-length moving window.To further enhance attack performance by incorporating more information available, Shang and Chen employed a range of historical nominal innovations to design linear attacks [49].They derived explicit solutions for optimal attack coefficients, eliminating the need for numerical optimization.The policy can achieve greater attack performance compared with [22], [48].However, the compromised innovation showed sequential correlations across consecutive steps, allowing the attack to bypass only single-step χ2detectors.
Owing to its simplicity, the linear strategy has also been adopted to synthesize FDI attacks that maximizeJh.This optimization presents greater complexity as the influence of the compromised measurements will keep propagating through the estimator dynamics.To address this problem, Li and Yang studied a linear attack strategy based on Gaussian distributions with arbitrary means [50].The optimal attack coefficients are determined through the application of the Lagrange multiplier method to solve a constrained quadratic optimization problem.Shanget al.examined a similar linear attack model, where the worst-case attacks without zero-mean constraints are analytically derived [54].The linear attack model has also found applications in various scenarios where attackers can deploy extra sensors to measure system states [35],[51], [53] and in optimal integrity attacks featuring relaxed stealthiness measured by the KL divergence [52], [54].
2)Dynamic Linear Attacks: Although substantial research efforts have been invested in synthesizing innovation-based linear attacks, the inherent linearity assumption significantly confines the feasible behaviors of attackers, and thus all these policies are not guaranteed to achieve the maximum attack performance globally.In order to address this limitation, Renet al.designed the compromised innovation as a linear combination of the current-step nominal innovation and a historically compromised one, resulting in adynamiclinear attack model [55].It can be proved that the attack generated by this model leads to an equivalent estimation performance degradation as the innovation-based approach that incorporates all historical data [49], but the dynamic one shows distinct advantages since it requires only two parameters to be determined at each step because of the recursive structure.
The dynamic model in [55] accommodates only the case of symmetric information, where the compromised innovation is designed based on only the eavesdropped measurements.Recently, a surprising finding by Zhouet al.revealed that the information-based optimal attack should be designed as an affine function of the MMSE estimate of the current-step compromised prediction error of RSE [56]–[58].A “separation principle” is proposed as a comprehensive design framework that can accommodate diverse information scenarios.The conclusion indicates that the worst-case attack performance depends on both the quantity of online information available and the width of the detection window.Furthermore,the compromised outputs can also be generated by the following linear time-varying (LTV) system:
whose coefficient matrices are fully determined offline by system parameters.
The preceding discussion primarily focuses on a simplified system model in Fig.2.Recently, numerous publications have delved into variations of the fundamental problem formulation, such as those involving partially secured channels [32],[59]–[63] and event-based estimators [26], [27], [64], [65].
3)Attacks on Partially Secured Channels: In this category,one representative scenario involves measurement data possessing different levels of confidentiality or being transmitted via different mediums to remote terminals.As a consequence,attackers can compromise only the unreliable channels but not the secured ones.In response to this scenario, Guoet al.devised an innovation-based linear attack strategy, which leverages additional equality constraints imposed by secure channels [59], [60].They provided explicit solutions for the optimal attack strategy and analyzed the relationship between the compromised estimation error covariance and the attacked sensors.To further enhance attack effectiveness, Xuet al.proposed the utilization of historical innovation intervals from both secure and insecure sensors to construct linear attacks[63].This approach is also capable of completely deceiving the sequential anomaly detector studied in [31].However, it should be noted that all the aforementioned attacks are formulated in a static linear format and are designed to maximizeJg.The derivation of optimal information-based attacks without the linearity assumption in the presence of secure channels still remains an open problem.
In practical cases, attackers may compromise only a subset of transmitted links simultaneously due to constraints on their energy or resources.Consequently, the allocation of attack power becomes a significant consideration.In light of this,Renet al.investigated a scenario where attackers could compromise at mostNout ofMchannels at each time, with the objective of maximizingJaat the fusion center [62].This problem was formulated as a Markov decision process (MDP)problem, and the existence of an optimal deterministic and stationary policy was established.
4)Attacks on Event-Based Estimators: Integrity attacks on event-triggered RSE can either modify the event-triggering mechanism or directly alter the transmitted data.In the former case, Chenget al.investigated an attacker’s objective to degrade RSE performance while evading detection based on communication rates [27].They obtained a closed-form relationship between the compromised event-triggering threshold and the nominal scheduling threshold.In the latter case, Shanget al.studied a more complicated scenario, where adversaries had the capability to launch DoS attacks, injection attacks, or a combination of both, subject to constraints on transmission rates and probability distributions [64].In contrast to prior Gaussian approximations [27], it is shown that the innovation in event-based RSE follows a complete Gaussian crater distribution, which forms the basis for analyzing the stealthiness properties of the proposed attacks.
There is also some work leveraging event-triggering techniques to design FDI attacks.A representative work is [26],where Zhaoet al.devised an event-triggered policy in which the optimal attack in [22] would be executed if a stochastic event-triggering condition was met.
5)Other Attack Scenarios: In the stochastic framework,stealthiness is defined based on the statistical properties of single or multiple-step innovations.This definition is consistent with the detection logic of χ2detectors, where innovations in a sliding window are utilized to construct the detection index.On the contrary, several studies adopt the KL divergence between the compromised and nominal innovation (or output) sequences as a measure of stealthiness [14],[66], [67].Some significant findings are presented in [14],[66], where Baiet al.quantified the upper bound of degradation in the worst-case scenario when an attacker ensures a specific level of stealthiness.In order to better evaluate the attack’s impacts on the estimation quality, Li and Yang designed an attack policy that maximizes the weighted combination of the average and terminal error covariance [68].Different from the previous attacks, the synthesis of the attack policy was not based on the historical measurements; the offline designed compromised signal was equivalent to adding an i.i.d.Gaussian noise to the nominal innovation.
The design of stochastic attacks largely depends on the formulation of the corresponding optimization problem.Generally, it is not appropriate to compare the effectiveness of attack policies if they adopt different stealthiness and performance metrics.In contrast to the deterministic attacks to be covered in the next section, these attacks typically necessitate the accessibility of online data to adversaries.This enables a“closed-loop” design aligning with our intuition: the greater the availability of online data, the more significant the potential for FDI attacks to cause estimation quality degradation.Future endeavors could be dedicated to researching stealthy attacks in distributed estimators and sensor networks, where more sophisticated detectors based on connectivity and topology information are employed to reveal anomalies.Moreover,it is worth pointing out that requiring compromised innovations to match nominal innovations statistically is sufficient(but not necessary) for maintaining the alarm rate (AR).Future studies that directly consider the stealthiness constraint on AR could possibly produce more destructive attacks.
B. Deterministic Attacks
The second approach for crafting stealthy deception attacks relies on deterministic system theory.This framework is better suited for designing integrity attacks that compromise systems characterized by bounded noises.By definingand∆zkrespectively as the state estimation difference and the residual difference between the compromised and nominal systems, the analysis of deterministic attacks can be achieved based on the following dynamic model [69]:
whereakdenotes the data injection in sensor channels andKis the estimator gain.This model originates from the linearity of LTI systems and is formulated by considering only the effects of attacks on system dynamics.The main objective is to determine whether there exists an attack sequence capable of causing the above system to exhibit unbounded states while maintaining bounded outputs.
1)Design of Stealthy Attacks: The pioneering work on vulnerabilities of linear-quadric Gaussian control systems was presented by Mo and Sinopoli [15], where the notions of(ϵ,α)-attackability and perfect attackability are defined.The paper also provided a necessary and sufficient condition for a system to be perfectly attackable, which depends on the unstable eigenvalues (denoted asλ) and eigenvectors ofA.Based on (6), a typical stealthy attack sequence independent of Ikis generated according to
whereρis a constant andμis determined by the eigenvector associated withλ.Motivated by [15], Huet al.gave a similar insecure definition for RSE and derived necessary and sufficient conditions for such property when all communication channels and partial channels are compromised [69].It should be highlighted that in these studies ∆zkhad to stay bounded.To completely mitigate the impact of FDI attacks on the detection function, Zhang and Ye introduced the concept of complete stealthiness, which further necessitates that limk→∞//∆zk//→0.This idea was later expanded upon to include energy stealthiness, which aims to deceive the summation (SUM) detector by maintaining a bounded level of accumulated attack energy [70].The study established both necessary and sufficient conditions for crafting FDI attacks with complete stealthiness and energy stealthiness.
Note that (6) is a dynamic system purely driven byak.The deterministic attack linked to (6) resembles what is commonly known as a “zero-dynamic attack”, typically executed on the controller side [71].This form of attack aims to deceive the controller by making the compromised control signal and sensor output appear consistent with the process’s nominal state.It is crafted using the zero dynamics of a system, where the output remains identically zero due to a specific combination of initial conditions and control inputs.Consequently, the process of synthesizing integrity attacks against RSE can be linked to the development of zero-dynamic attacks in controller channels.
2)Reachable Set Analysis: In addition to the design of stealthy attacks, noticeable research efforts have been devoted to analyzing the maximum state deviations caused by these attacks [72]–[75].In [73], Kwonet al.considered three kinds of stealthy attacks according to the attackers’ ability to compromise the system.They presented a method to evaluate the reachable error region for sensor-only attacks by formulating a stochastic optimal control problem.Following this study,many endeavors have been undertaken to investigate security concerns within control systems by analyzing reachable sets.For instance, Mo and Sinopoli studied the effect of stealthy integrity attacks on CPSs and demonstrated that the attacker’s strategy can be formulated as a constrained control problem;the characterization of the maximum perturbation can be posed as reachable set computation, which is solved by ellipsoidal approximation methods [74].In [75], Murguiaet al.proposed two security metrics to quantify the potential impact of stealthy attacks: the volume of the attacker’s reachable set and the minimum distance to critical states.The authors also provided synthesis tools to redesign controllers and monitors such that the impact of stealthy attacks is minimized and the desired attack-free performance is guaranteed.
3)Other Scenarios: The deterministic design framework has also been extended to distributed systems.In [76], Wanget al.studied a slightly different scenario that attackers can corrupt both the output measurements and the state estimates in distributed state estimation.The authors derived necessary and sufficient conditions for the vulnerability of the system under different attack scenarios.
Based on (6), Chenet al.studied a scenario where attackers aim to regulate the estimation error to a value arbitrarily defined by them, which can reduce the likelihood of detection by amplitude detectors [77].They used dynamic programming to derive an explicit expression for the optimal attack sequence and also analyzed its convergence and feasibility.
While most of the relevant studies focus on the conditions whether there exists an attack sequence causing instability in estimators, there is also some work investigating the maximum state estimation deviation in a finite horizon.In this case, the design of attack policies is based on solutions to an optimization problem.A representative study is presented in[78], where the optimal deterministic attack is derived bymaximizing a quadratic objective function subject to energy constraints.

TABLE II DESIGN OF STEALTHY INTEGRITY ATTACKS ON RSE
Deterministic attacks are typically created by exploiting the control system’s unstable modes.These attack signals can be fully determined without the need for knowledge of the online transmitted data, which differentiates it from stochastic attacks.However, this “open-loop” design may lack robustness in terms of maintaining stealthiness properties.To determine the unstable eigenvalues and eigenvectors of the system matrix, attackers have to possess highly precise information about the system parameters.Otherwise, self-generated attacks may not be able to consistently keep the residual within bounded limits.
Different attack approaches in the two frameworks are summarized in Table II, where the classification is based on the attack model, performance measure, stealthiness metric, the existence of side information, and the existence of secured transmission channels.
IV.DEFENSIVE COUNTERMEASURES
While extensive research has been dedicated to exploring integrity attacks, these studies have significantly contributed to our comprehension of inherent vulnerabilities within RSE.As a result, many effective techniques have been introduced in the past decade to enhance the security of RSE.It is seen that a unified design framework for countermeasures is lacking,with scholars from diverse disciplines making significant contributions through different techniques.
For general linear descriptor systems, Pasqualettiet al.proposed a mathematical framework for CPSs, attacks, and monitors, and characterized the fundamental limitations of monitoring from system-theoretic and graph-theoretic perspectives[20]; both centralized and distributed monitors that can detect and identify attacks were designed.In [82], Fawziet al.investigated the problem of state estimation for linear systems when some of the sensors are compromised by adversaries.The authors provided an efficient algorithm inspired by techniques in compressed sensing and error correction to estimate the state of the plant despite attacks.Recently, this detection framework has been extended to more general cases where the compromised sensors can change over time and the attack signals can be arbitrary and unbounded [83].
Regarding the enhancement of RSE security, notable countermeasures include watermarking-based defense [84]–[90],encryption-based defense [91]–[93], moving-target defense(MTD) [94]–[97], and a range of other approaches.Since integrity attacks are intentionally synthesized to deceive traditional passive detectors, most of these countermeasures aim at creating a proactive defense mechanism.As will be discussed later, the enhancement of system security using proactive methods often comes at the expense of sacrificing some other aspects of performance, e.g., control and estimation quality loss, or extra resource consumption.
A. Watermarking-Based Defense
Watermarking referring to the technique of embedding secret data into a carrier signal, such as audio, video, or image data, is a widely adopted method in information security to prevent contents from unauthorized modification.The pioneering work of adopting this technique to CPS protection is[84], where Moet al.designed a watermarking signal that is superimposed on the optimal control input and has statistical properties that maximize the detection performance while satisfying a constraint on the control performance.An optimal Neyman-Pearson detector that can determine if the system is under attack by comparing the observed and expected outputs is derived.Similarly, in [85] a secret noisy i.i.d.input is added to the optimal control signal.If the process is operating under normal conditions, the system operator should be able to detect the presence of the watermark in the sensor measurements.In order to defend against powerful adversaries who can read a subset of control inputs to design stealthy attacks,Weerakkodyet al.proposed a robust physical watermarking based on the Neyman–Pearson criterion; a convex optimization problem to obtain the watermark signal was formulated[86].
The successful application of watermarking-based defense has been demonstrated in [88], where Ahmedet al.implemented the watermarking signal on a real water distribution testbed.The technique is shown to achieve a 100% true positive rate and a low FAR in detecting replay attacks while preserving the system performance and meeting consumer demand.Recently, this method has been extended to the cases of dynamic watermarking to protect linear-parameter-varying systems [89] and simultaneously online watermarking design and system identification [90].
It is worth emphasizing that the achievability of enhancing security using watermarking is often at the expense of nominal system performance degradation.Given these tradeoffs,the decision to use watermarking for security purposes should be carefully considered in the context of the specific application and its requirements.It is important to strike a balance between security and performance, taking into account factors like the sensitivity of the data, the resources available, and the control signal saturation.
B. Encryption-Based Defense
In essence, the goal of data encryption/decryption-based defense is to make the intercepted data as difficult to decipher as possible, thereby enhancing the overall security of the system.Only those who possess the encryption key can decrypt the ciphertext back into its original form.Regarding CPS security, this technique is similar to coding/decoding-based defense, while the latter does not require secret keys to recover the original information.Based on this idea, Miaoet al.proposed a low-cost method of coding the sensor outputs to detect stealthy FDI attacks.They showed the conditions for a feasible coding matrix that can increase the estimation residues under intelligent data injection attacks and provided an algorithm to compute such a matrix.The paper also presented a time-varying coding scheme to defend against attackers who can estimate the coding matrix from intercepted online data [91].
To defend against the extensively studied innovation-based linear attacks, Shanget al.studied a linear encryption approach to bolster the security of RSE, aiming to safeguard transmitted data against unauthorized alterations [92].This linear encryption technique, synthesized by minimizing the worst-case estimation errors, was developed through the Stackelberg game analysis.Recently, this technique was extended to protect data transmission of traditional sensors by encrypting a subset of packets, which can strike a balance between resource utilization and security enhancement [93].
It is important to note that encryption-based defense strategies involve the incorporation of additional modules dedicated to data encryption and decryption.The hardware and computational resources required for these processes should be regarded as the overhead incurred in pursuit of heightened security.Moreover, the delays induced by data processing should also be taken into account in real-time systems.In practical scenarios, system defenders should carefully adjust their designs to achieve a favorable equilibrium between these performance metrics.
C. Moving-Target Defense
MTD is a proactive strategy designed to enhance the security of computer systems and networks by frequently changing the attack surface and making it more difficult for adversaries to identify and exploit vulnerabilities.The core idea behind MTD is to create a dynamic and unpredictable environment for potential attackers.Following this idea, Tianet al.proposed an approach that actively changes the system configuration to invalidate attackers’ knowledge about the system and detect Stuxnet-like attacks [94].The paper showed that MTD can deal with different types of attacks, such as measurement-independent stealthy attacks, control scaling attacks,and measurement replay attacks.In [95], the authors proposed to introduce extraneous states with time-varying dynamics that are unknown to the adversary but known to the defender and use additional sensors to measure these states.
More recently, Kanellopoulos and Vamvoudakis proposed a secure control algorithm for CPSs facing sensor and actuator attacks [97].The technique integrated proactive and reactive defenses, with the proactive part using stochastic parameter adjustments to enhance unpredictability and the reactive part detecting attacks via an integral Bellman error computation.To analyze system properties when implementing MTD, the theory of switched systems is frequently employed.This adaptation allows for the examination of stability concerns associated with changes in system configurations.
MTD is an effective approach to defend against cyberattacks.However, one of its drawbacks is that it can potentially lead to suboptimal system performance when there are no active cyber-attacks.It also introduces extra challenges, as frequent changes in system dynamics or configuration can complicate the design of defense strategies and the analysis of the system’s normal behavior.
D. Other Defense Methods
It is seen that a unified framework to design countermeasures against cyber-attacks does not exist.Researchers from diverse disciplines contribute through different techniques[29], [31], [83], [98]–[104].Among the work beyond the scope of proactive detection mechanism, some approaches aim to enhance the performance of traditional detectors through appropriate modifications [98]–[100].A representative work is presented by Ye and Zhang to detect deterministic FDI attacks [100].They introduced a SUM detector, which uses both the current and historical information and has a statistical property that its evaluation value satisfies χ2distribution when the system is normal and increases to infinity when the system is under attack.The superiority of the proposed method is demonstrated by the fact that two types of FDI attacks can be detected by the SUM detector but not theχ2one.
Detecting stealthy attacks becomes relatively easier when secured transmission channels are in place.Correlations between data packets in both safe and unsafe channels can be leveraged to design a detection mechanism [31], [101], [105].Based on this idea, Liet al.proposed three sequential dataverification and fusion procedures for different detection scenarios [31].This important work serves as a benchmark for many follow-up studies on defense against innovation-based linear attacks.For instance, Guoet al.introduced a Gaussianmixture-model based detection mechanism [101].The expectation–maximization algorithms are applied to cluster the local estimates from different sensors and assign a belief for each sensor, which is used to fuse the measurements accordingly.More recently, Chattopadhyay and Mitra introduced an online learning-based algorithm for secure state estimation [106].The proposed method can accommodate the case where no safe sensors are in place and offers up to 3-dB improvement in MSE compared with [31].However, it is worth pointing out that all these methods assume adversaries adopt the innovation-based linear model.The effectiveness of the countermeasures against broader attack types, such as dynamic linear attacks, should be re-examined in future studies.

TABLE III REPRESENTATIVE COUNTERMEASURES AGAINST CYBER-ATTACKS
In distributed state estimation, the information from neighboring sensors can be utilized to build a detection mechanism[29], [107].In [29], Yanget al.designed a protector for each sensor based on the online innovation from its neighboring sensors.A sufficient condition for the stability of the estimator equipped with the proposed protector under hostile attacks was provided, and a critical attack probability that corresponds to a given steady-state estimation error covariance was derived.
The detection of integrity attacks has been studied using data-based methods [108], [109].In situations where sufficient online data is collected, Shiet al.proposed transfer entropy countermeasures for anomaly detection under various attacks [109].The transfer entropy is utilized to measure causality or information flow between sensor measurements or innovation sequences.The results showed how attacks can disturb the causality and change the transfer entropy values.
Finally, there are also a few studies investigating attack defense in a game-theoretic framework.A representative work is presented in [110], where Liet al.modeled the interaction between the defender and the attacker as a Stackelberg game,where the defender allocates defense resources to secure sensors and the attacker chooses target sensors to attack.They analyzed the optimal solutions for both sides under different types of budget constraints and transformed the game into linear programming problems.
The effectiveness of defensive measures varies depending on specific attack scenarios.Some techniques are developed to ensure that adversaries cannot satisfy the corresponding stealthiness condition easily.Therefore, the method may fail to defend against more sophisticated attackers that employ a stricter stealthiness measure.In practical cases, the continuous interplay between attackers and defenders makes the design of defensive measures a topic of enduring significance in the control community.
Different countermeasures against cyber-attacks are summarized in Table III, where the relevant references, the type of attacks to be defended, the main techniques adopted, and a few comments on their limitations are listed.
V.BEYOND INTEGRITY ATTACKS
In this section, we briefly review the design of DoS and eavesdropping attacks and the corresponding countermeasures in the basic problem setup.Interested readers may refer to [25], [119] for event-based estimators and [28], [64],[120]–[123] for hybrid DoS and FDI attacks against RSE.
A. Denial-of-Service Attacks
1)Design of DoS Attacks: Synthesizing DoS attacks from an adversary’s perspective can be formulated as a constrained optimization problem, where the attacker aims to maximize the impact on the target system under various constraints, as illustrated by
where ∆ represents the total power budget.The constraint on the packet-reception rate (P RR) is imposed with the awareness that, in real-world systems, a DoS attack causing an excessively low PRR at the terminal can be readily detected by alarm systems.
In [124], [125], Zhanget al.derived the optimal attack schedule under a limited energy budget; they also studied the case where the estimator has an intrusion detector that triggers an alarm when the PRR falls below a threshold.In this context, the attacker’s behavior is symbolized through a binary sequence.At each step, adversaries make a straightforward choice between “attack” or “not attack” to determine whether to completely obstruct the transmission channels.Consequently, the optimal attack schedule design becomes an integer programming problem, which is in general difficult to solve.However, in [125] the authors presented some structural results, showing that grouping the attacks leads to the maximal effect, while separating the attacks as uniformly as possible leads to minimal degradation.In [126], the authors explored optimal strategies for an invader launching DoS attacks on a centralized sensor network to degrade system performance.They provided an analytical solution for single-sensor systems and numerical methods for multiple-sensor systems, both with attack energy constraints.
One property of wireless communication is that the packet can experience random loss due to channel fading, interference, scattering, and other factors [127].To explore more realistic scenarios, some researchers adopt the assumption that adversaries can manipulate the interference or noise power in signal-to-interference-plus-noise ratio (SINR) channels, where the packet dropout rate is determined by both the strength of desired signals and the level of interference power [128].For such channels, Zhanget al.analyzed the impact of DoS attack power on the estimation accuracy and energy efficiency of the sensor, and found a critical value of attack power that determines the stability of the RSE [129].The result is based on a well-known conclusion that an excessively low PRR for the Kalman filter with intermittent observations will lead to unbounded estimation errors [130].
To compromise SINR-based channels with limited energy,Penget al.formulated the problem of finding the optimal attack power schedule subject to average energy constraints as an MDP [131].They proved the existence and uniqueness of an optimal deterministic and stationary policy for attackers and showed that the optimal policy has a threshold structure.Liuet al.also formulated the problem of designing optimal DoS attacks as an MDP with a discount factor to balance the current and future rewards [132].The optimal solution is obtained based on the Bellman’s optimality principle.
2)Defensive Countermeasures: Unlike FDI attacks that can deceive anomaly detectors, maintaining stealthy is usually not a primary concern in the design of DoS attacks.Consequently,the majority of research on defense countermeasures primarily addresses the challenge of ensuring reliable estimation performance in the presence of attacks.
When CPSs are subjected to DoS attacks, changes in the measurement or control input matrices lead to deviations of system dynamics from their normal conditions.Therefore, the switched system theory is often applied for attack-resilient estimation [133], [134].This approach models the system as one that alternates between normal and attacked states, especially during intermittent DoS attacks.The primary objective is to analyze the stability of a dynamic system operating under these conditions.A representative work is [133], where Chenet al.proposed a switched system method for the fusion estimation of phaser measurement units in power systems.The switching rule is based on the innovations of an extended Kalman filter, with the goal of achieving a balance between metrics concerning the estimation accuracy, convergence speed, and computation time.
3)Game Theoretic Analysis: Notably, it is found that massive publications studied the interactive actions of attackers and defenders in a game-theoretic framework [36], [37],[115]–[118].The pioneering work is [36], where Liet al.regarded the attack and defense problem as a zero-sum game and proved the existence of a Nash equilibrium.They used Markov chain theory to solve a relaxed problem.This framework was further extended to the case of SINR transmission channels [37], where a modified Nash Q-learning algorithm was applied to solve the Markov game over an infinite time horizon.
In multiple-channel transmission scheduling, Dinget al.also modeled the interaction between the sensor and the attacker as a two-player stochastic game and used a Nash Qlearning algorithm to find the optimal strategies [116].To study the asymmetric information scenario, the stochastic Bayesian game has been utilized to characterize the strategic interaction between two players in RSE [117].In this case, the sensor possesses acknowledgment information from the estimator, while the attacker does not.Recently, Yuanet al.considered a more practical case in which communication networks are time-varying; the long-term interaction of players is modeled with a Markov game [115].An online minimax Qlearning is applied to solve the problem.
B. Eavesdropping Attacks
It is commonly held that the states of the system are treated as sensitive information, which should not be accessible to adversaries.Nevertheless, an attacker who can eavesdrop on the sensor measurements can execute estimation algorithms to gain such confidential information.
1)Design of Eavesdropping Attacks: There are relatively few studies on the synthesis of optimal eavesdropping attacks.One reason is that stealthiness is usually not a primary concern; thus the attack design often boils down to a standard state estimation problem.In practical cases with secured data transmission, considering that deciphering encrypted data is often resource-consuming, Zhouet al.studied the optimization problem from adversaries’ perspective under energy constraints [23].The authors analyzed the impact of different decryption strategies on eavesdropping performance and proposed a deciphering schedule that minimizes the expected estimation error without exceeding the energy budget.
In [135], Dinget al.studied an intelligent attacker who can switch between passive and active modes to enhance eavesdropping while evading PRR-based detection.They modeled this trade-off as a constrained MDP and derived conditions for a policy that meets stealthiness requirements and maximizes eavesdropping efficiency.Other relevant studies on the synthesis of eavesdropping attacks in different scenarios can be found in [136], [137].
2)Optimal Scheduling Based Defense: The majority of current research on eavesdropping attacks on RSE is formulated from the defender’s standpoint, and a typical problem is stated as follows:
where an optimal sensor schedule within the power budget ∆is one in which the estimation error for adversaries (EAttack) is maximized while ensuring that the estimation error for RSE(ERSE) does not surpass a specified threshold.In essence, The optimal scheduling-based defense boosts RSE confidentiality by reshaping sensor transmission decisions, which can balance various indices for optimal overall performance [138]–[141].
Using the above framework without power constraints, Tsiamiset al.introduced a control-theoretic definition of secrecy for RSE, which requires that the user’s estimation error is bounded while the eavesdropper’s estimation error is unbounded [138].The paper studied a simple secrecy mechanism that randomly withholds measurements from being transmitted.It was proved that the proposed mechanism can achieve perfect expected secrecy if the user’s PRR is higher than the eavesdropper’s P RR.
Using a linear combination ofERSEandEAttackas the performance metric, Leonget al.derived structural results on the optimal transmission policy, which shows a thresholding behavior in the estimation error covariances [139].The paper also proved that in the situation of infinite horizon, there exist transmission policies that can keep the expectedERSEbounded while the expectedEAttackbecomes unbounded.
Taking the transmission power into consideration, Wanget al.proposed a problem formulation that considers the estimation errors of both parties and the cost of the sensor’s transmission energy [140].The authors proved that there exist some structural properties for the optimal transmission schedule, such as threshold and switching behaviors, for both the known and the unknown eavesdropper’s estimation errors.
3)Encryption-Based Defense: The above scheduling-based defense usually enhances the confidentiality of RSE at the cost of a slight reduction in nominal estimation performance.To ensure an optimal state estimation for defenders, there are also plenty of studies considering encrypting the transmission data to defend against eavesdropping attacks [111]–[114].A representative method is presented in [112], where Tao and Ye proposed to protect the RSE from eavesdropping attacks by using time-varying coding and noise-adding techniques.They also derived the minimum encoded dimension and the upper bound of the update period for the time-varying coding scheme.
Note that the above method requires that the coding matrix not be accessible to adversaries.In order to defend against more powerful attackers, encryption-based methods are adopted in [113], [114].Zouet al.proposed a novel encryption-decryption scheme (EDS) to protect the transmitted data from eavesdropping, using artificial noise injection and secret keys; they designed a finite-horizon energy-to-peak state estimator for LTI systems under EDS.Sufficient conditions for the existence of the EDS and the state estimator are obtained[113].Recently in [114], Shang and Chen proposed linear encryption strategies to protect the transmitted data from eavesdropping.For two types of data transmission, the authors obtained the optimal filtering for the eavesdropper and designed the encryption coefficients by maximizing the eavesdropper’s estimation error covariance.
The application of privacy-preserving techniques in realworld systems can be found in [142], where Sunet al.introduced a novel privacy-preserving algorithm for distributed economic dispatch in microgrids.The authors provided convergence proof, analyzed privacy levels within a differential privacy framework, and demonstrated effectiveness using an IEEE 39-bus system.
VI.CONCLUSIONS AND FUTURE WORKS
The security issue in CPSs is a multidisciplinary topic that requires collaboration of experts from diverse fields, including computer engineering, cryptography, communication, and others.Moreover, domain-specific knowledge from vulnerable industrial sectors, such as energy pipelines and smart grids, is also essential for us to comprehensively understand the execution of these attacks and the mechanisms required for effective protection.This paper discussed the current research status on the design of cyber-attacks against RSE and the corresponding defensive countermeasures.The relevant problems with single-sensor scenarios as well as different variants have been reviewed from both attackers’ and defenders’ perspectives.It is observed that optimization-related tools and algorithms play a central role in the majority of existing studies.
Though many elegant results have been derived, the applicability of these methods in enhancing the security of realworld systems has not been adequately verified.Almost all existing studies validate the effectiveness of proposed methods using a simplified process model.The design of cyberattacks against state estimators are discussed in smart grids[1], remotely piloted vehicles [77], and IEEE 6 bus power systems [70]; the defensive countermeasures can be found in unmanned aerial vehicles [83], the Tennessee Eastman challenge problem [85], [109], water distribution systems [44],[88], IEEE 39-bus systems [94], [142], aircraft [97], [108],smart grids [98], [102], and artificial neural networks [121].Specifically, Dinget al.outlined a secure state estimation framework for water distribution systems in the presence of unknown disturbance inputs, measurement noises, and malicious attacks [44].The process was modeled by an LTV system and the secure state estimation problem was cast into the feasibility of a recursive convex optimization problem subject to a series of LMIs.In the future, more efforts are needed to verify the effectiveness of these techniques in practical systems.
In the following, a few topics that have not been sufficiently investigated in existing work are presented.
A. Data-Driven Design
Most of the existing studies, whether focusing on the design of optimal attacks or defensive measures, presume that a dynamic model is available to both adversaries and defenders.Nonetheless in practical systems, an accurate system model is difficult or even impossible to obtain, especially for large and complex industrial processes.This is particularly difficult for attackers who usually have only limited access to system knowledge.Therefore, studying cyber-security with partial knowledge of system parameters or pure data-driven methods is a meaningful topic [143]–[147].
B. Robust Design
In the model-based approaches to cybersecurity, a majority of them consider the cases that the model possessed by attackers and defenders to be accurate.Based on this assumption,one can design strictly stealthy attacks and countermeasures.However, in practical cases, uncertainties in the model parameters have a great impact on the stealthiness property.In the deterministic framework for designing integrity attacks, the boundness of residuals is achieved by the cancellation of two unbounded attack signals in the direction of unstable eigenvectors.Therefore, even a minor inconsistency in calculating these eigenvectors can prevent the attacks from maintaining residuals within bounded limits consistently.Future research should explore robust stealthiness and defensive measures in the context of model uncertainties [148], [149].A representative study is presented in [149], where a novel class of resilient estimation algorithms is designed when there exist uncertainties in system matrices.
C. Imperfect Transmission Channels
The majority of existing results assume that, under nominal conditions, the transmission channel is perfect without delays and packet dropouts.However, the influence of such imperfections on the design of optimal attacks and defensive measures has not been thoroughly studied yet.Future endeavors could be dedicated to analyzing the effects of cyber-attacks in imperfect wireless links.This investigation will enhance the applicability of the related theoretical research to real-world systems.
D. Modern Industrial Alarm Systems
Industrial alarm systems are commonly used to provide timely alerts when faults occur in industrial processes.Nowadays, most alarm systems are designed to minimize the impact of faults and improve the effectiveness of corrective responses for field workers [150].As has been pointed out by many industrial experts, there is an urgent requirement to safeguard industrial facilities from cyber-attacks.In future work, it would be valuable to create an integrated platform that combines alarm management tools and fault/attack detection algorithms.This integration aims to prompt the delivery of alerts in case of any abnormal events by making full utilization of available information from different sources and leveraging techniques in different disciplines.
 IEEE/CAA Journal of Automatica Sinica2024年4期
IEEE/CAA Journal of Automatica Sinica2024年4期
- IEEE/CAA Journal of Automatica Sinica的其它文章
- When Does Sora Show:The Beginning of TAO to Imaginative Intelligence and Scenarios Engineering
- Goal-Oriented Control Systems (GOCS):From HOW to WHAT
- Digital CEOs in Digital Enterprises: Automating,Augmenting, and Parallel in Metaverse/CPSS/TAOs
- A Tutorial on Federated Learning from Theory to Practice: Foundations, Software Frameworks,Exemplary Use Cases, and Selected Trends
- Data-Based Filters for Non-Gaussian Dynamic Systems With Unknown Output Noise Covariance
- Designing Proportional-Integral Consensus Protocols for Second-Order Multi-Agent Systems Using Delayed and Memorized State Information
